
Understanding Business Email Compromise (BEC) Scams and How to Protect Your Organization
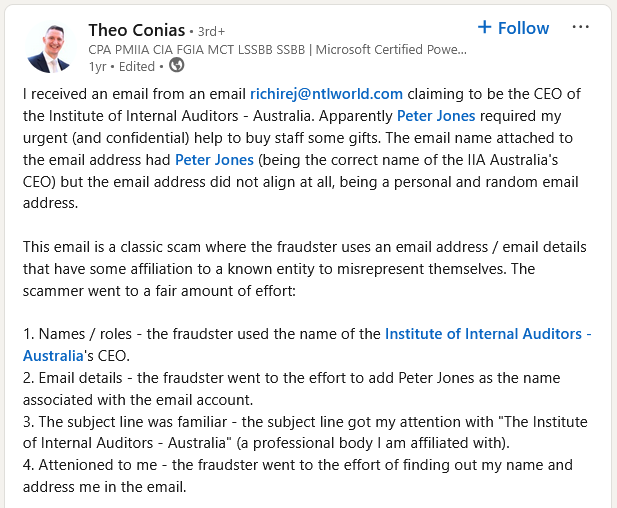
In this article, we will cover:
- What Business Email Compromise (BEC) scams are
- Why they are becoming more common
- How these scams work
- Related cyber threats
- How cybersecurity solutions can help protect organizations from these attacks
Before we dive deeper, let’s first understand how these scams operate and why they pose a serious threat to businesses worldwide.
What is Business Email Compromise (BEC)?
Key Characteristics of BEC Scams
- Impersonation – Attackers pose as senior executives, business partners, or vendors.
- Manipulated Email Details – Fraudsters use fake email addresses that resemble legitimate ones.
- Urgency & Secrecy – The emails create a sense of urgency, discouraging verification.
- Financial Requests – Requests often involve payments, wire transfers, or gift card purchases.
- Minimal Technical Red Flags – Unlike malware-based attacks, BEC scams rely on social engineering rather than malicious links or attachments.
Why Are BEC Scams Increasing?
How BEC Scams Work
Fraudsters send emails with urgent or confidential requests, often using excuses like:
- Fake invoice payments (e.g., “Urgent wire transfer needed for vendor payment.”)
- Payroll fraud (e.g., “Please update my bank account for this month’s salary.”)
- Gift card scams (e.g., “I need you to buy gift cards for a company event.”)
Other Related Cyber Threats
How to Identify a BEC Scam
- Unexpected Emails – If an email from an executive or vendor is out of the blue, be cautious.
- Urgency & Secrecy – Any request pressuring immediate action without verification is suspicious.
- Unusual Requests – Payments, gift card purchases, or bank account changes should always be double-checked.
- Poor Grammar & Spelling – Subtle mistakes often indicate fraud.
- Inconsistent Email Domains – Check if the email is from a legitimate business domain.
- Lack of Email Signatures – Official emails usually have proper signatures and contact details.
What Should You Do If You Receive a Suspicious Email?
✅ Do Not Reply – Avoid engaging with the sender.
✅ Verify Through Another Channel – Contact the sender via phone or LinkedIn.
✅ Report It – Inform IT teams, cybersecurity personnel, or use platforms like Scamwatch.
✅ Block the Sender – Prevent further communication from the suspicious email.
How Cybersecurity Solutions from Accuract Technologies Can Protect Your Business
Accuract Technologies offers robust cybersecurity solutions to help businesses safeguard their email systems and prevent BEC attacks.
1. Email Security & Threat Detection
- Advanced AI-powered email filtering to detect and block BEC, phishing, and spoofing attacks.
- DMARC, SPF & DKIM authentication to prevent unauthorized email usage.
2. Employee Awareness & Training
- Security awareness programs to help employees recognize social engineering tactics.
- Simulated phishing attacks to test and improve email security awareness.
3. AI-Powered Fraud Detection
- Behavioral analytics to detect unusual email patterns and stop fraud before it happens.
- Real-time alerts for suspicious financial transactions.
4. Multi-Factor Authentication (MFA) & Access Control
- MFA implementation to secure email accounts and prevent credential theft.
- Zero Trust security model to restrict unauthorized access.
5. Incident Response & Cybersecurity Consulting
- 24/7 monitoring and rapid incident response to handle BEC attacks.
- Expert cybersecurity consultation to strengthen business defenses.
Conclusion
Accuract Technologies provides Advanced Cybersecurity Solutions to protect businesses from evolving email-based threats. With AI-powered fraud detection, email security, and proactive monitoring, your organization can stay ahead of cybercriminals and safeguard critical business communications.
For expert cybersecurity solutions, contact Accuract Technologies today!
Email: reach@accuracttech.com
Phone: +91 77022 93372
Website: accuracttech.com
